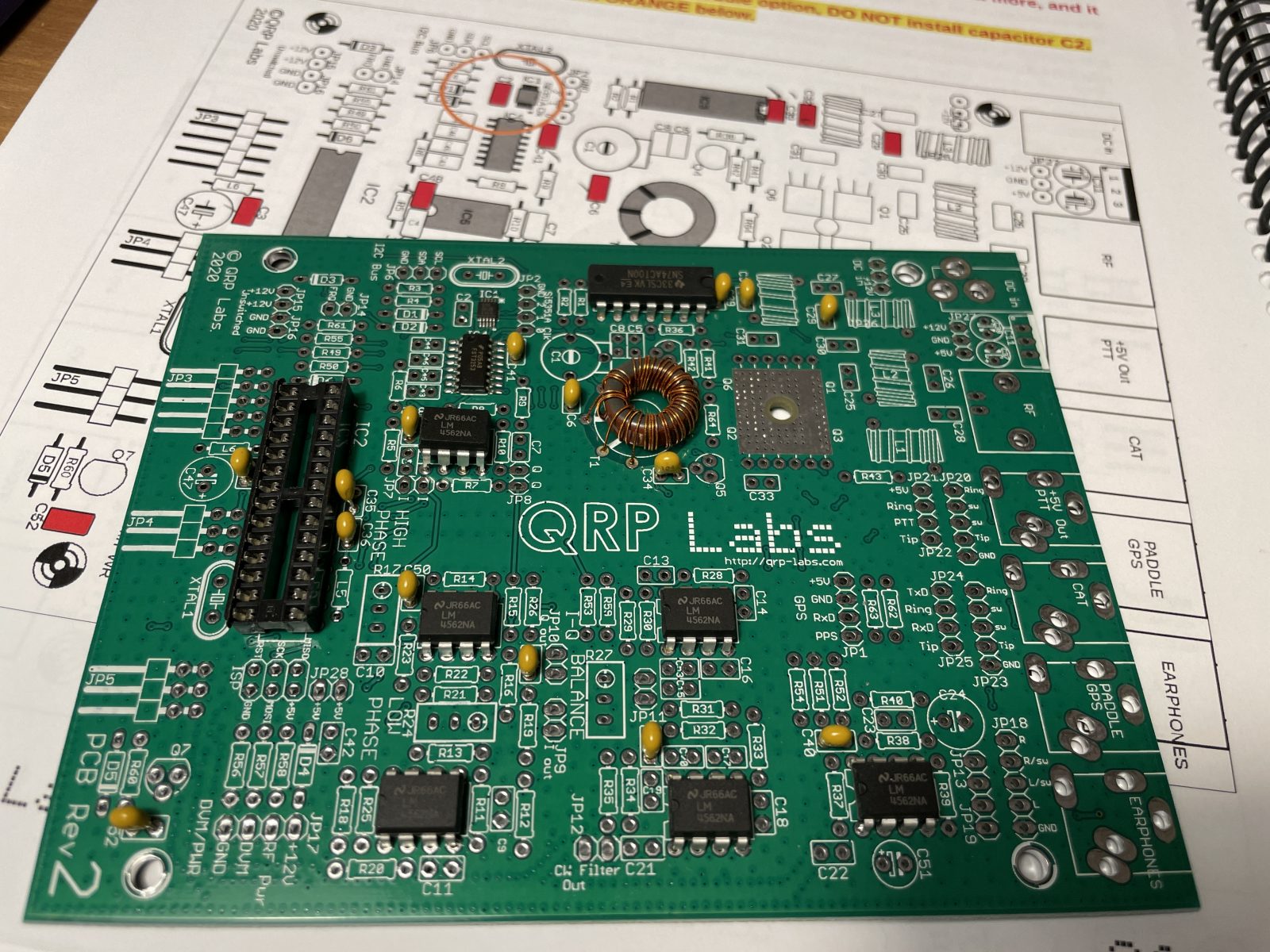
QCX+ 5W CW transceiver kit
During one of my CW classes, a couple of my students were waxing on about the fun they had in assembling a QRP Labs QCX+ radio kit. They invited me to participate in the fun. Although I’ve done small kits in the past, this was much more ambitious. I was leery what paltry soldering skills […]
QCX+ 5W CW transceiver kit Read More »